The only Dynamic Machine Identity Provider for
Securely automate, move data, and connect with confidence from anywhere to anywhere.
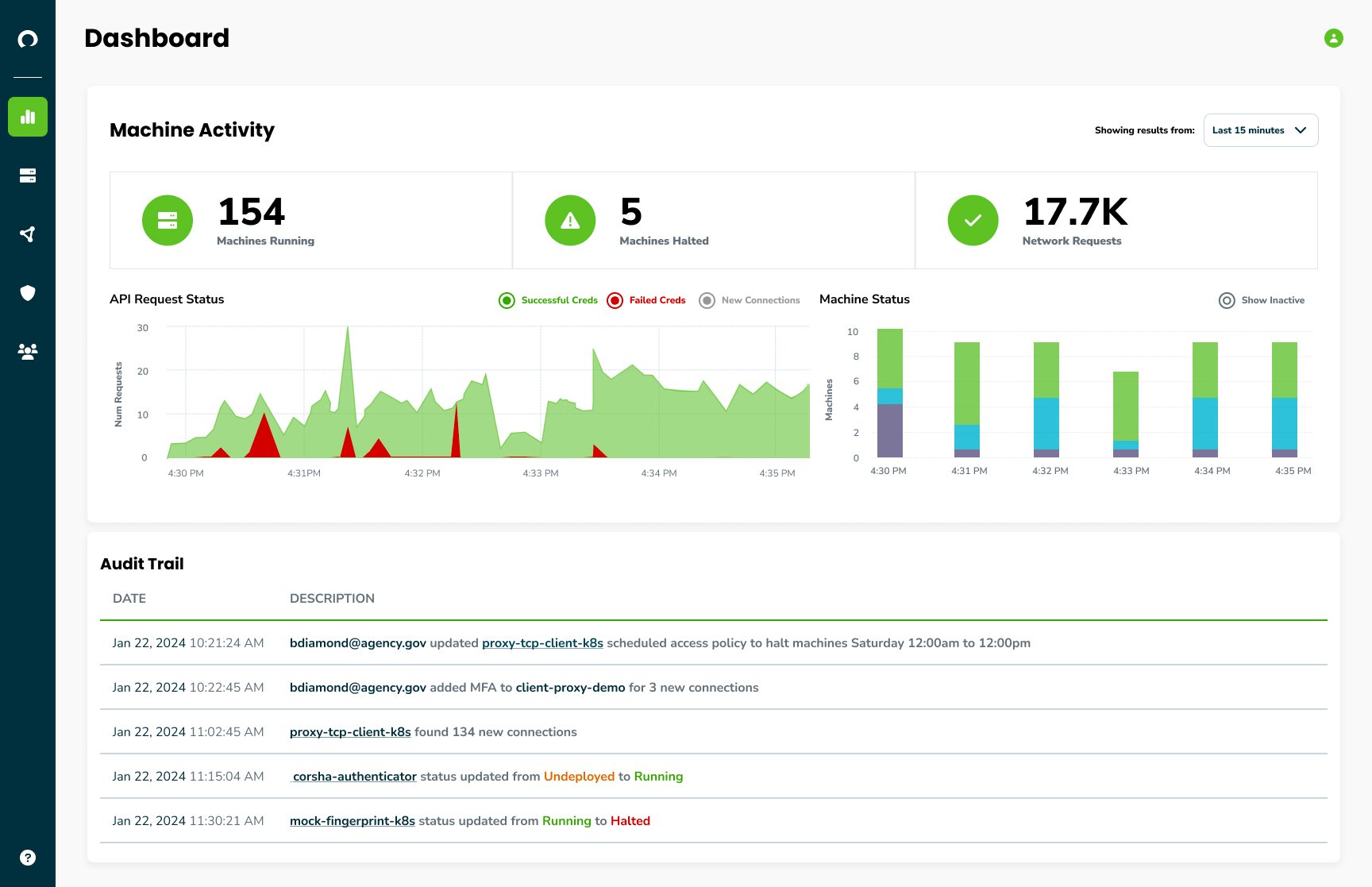
Push past simple secrets and focus on identity and access.
-1.png?width=267&height=191&name=Vector%207%20(1)-1.png)
Dynamic Machine Identities
Manage identities and access, not secrets, through Corsha’s Identity and Access Management Platform for your core infrastructure.
.png?width=267&height=191&name=Vector%209%20(1).png)
Discover and Audit Connections
Find, protect, and continually audit all of your machine-to-machine connections in real-time whether they are east-west or north-south.
-1.png?width=267&height=191&name=Vector%207%20(1)-1.png)
Enforce one-time-use credentials for Machines
Move past static secrets and painful secrets management tools to enforce one-time-use credentials for your machine-to-machine communications.
.png?width=267&height=191&name=Vector%209%20(1).png)
Manage and schedule Access
Manage all access to protected systems and services without having to worry about rotating or revoking secrets across 100’s of client workloads. Start, stop, and even schedule remote access to machines, systems, and services.
-1.png?width=267&height=191&name=Vector%207%20(1)-1.png)
Deploy Anywhere
Easily integrated into any environment with the deployment option that suits you best. Offered as both as SaaS - Corsha Cloud for hassle-free cloud-based security or fully on-premise as Corsha Enterprise.
Ready to learn more? Dive into the future of machine identity for a hybrid world
WHY?
Your core communication is machine-to-machine, over 90% in fact.
Invest in Machine IAM for your shop floor, enterprise, and cloud today.

0%
Trusted By












Real reviews, real results—find out why customers rely on Corsha.
%20(1)%20(1).jpg?width=1200&height=1284&name=imgpsh_fullsize_anim2%20(1)%20(1)%20(1).jpg)
William Potter
Lead Engineer, Federal
Since implementing Corsha solutions in our zero trust lab demo environment for Lumen’s public sector customers, our zero trust lab architecture has been significantly enhanced. Corsha’s platform for non-human identity has enabled us to secure long-lived API secrets and obtain visibility on client connections.
Awards





Resources
Explore the latest in machine identity and API security resources. Discover articles, white papers, case studies, and more to level up.
