The Enterprise Identity Provider focused on Machines
The Future of Machine Identity for a Hybrid World
.png)
.png)

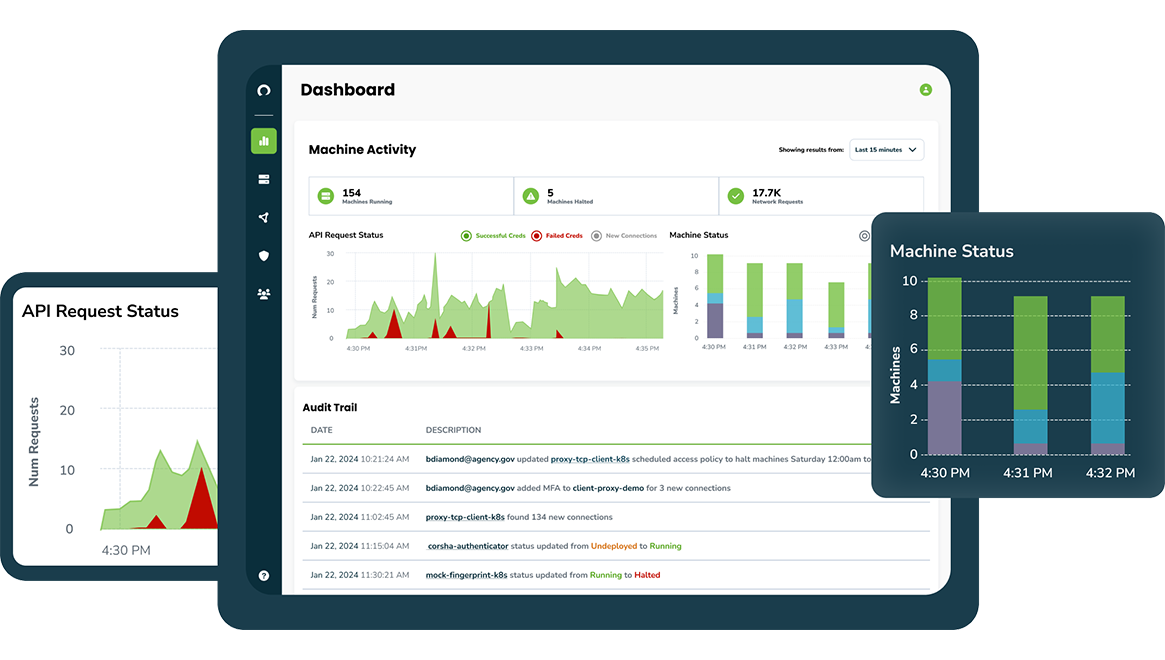
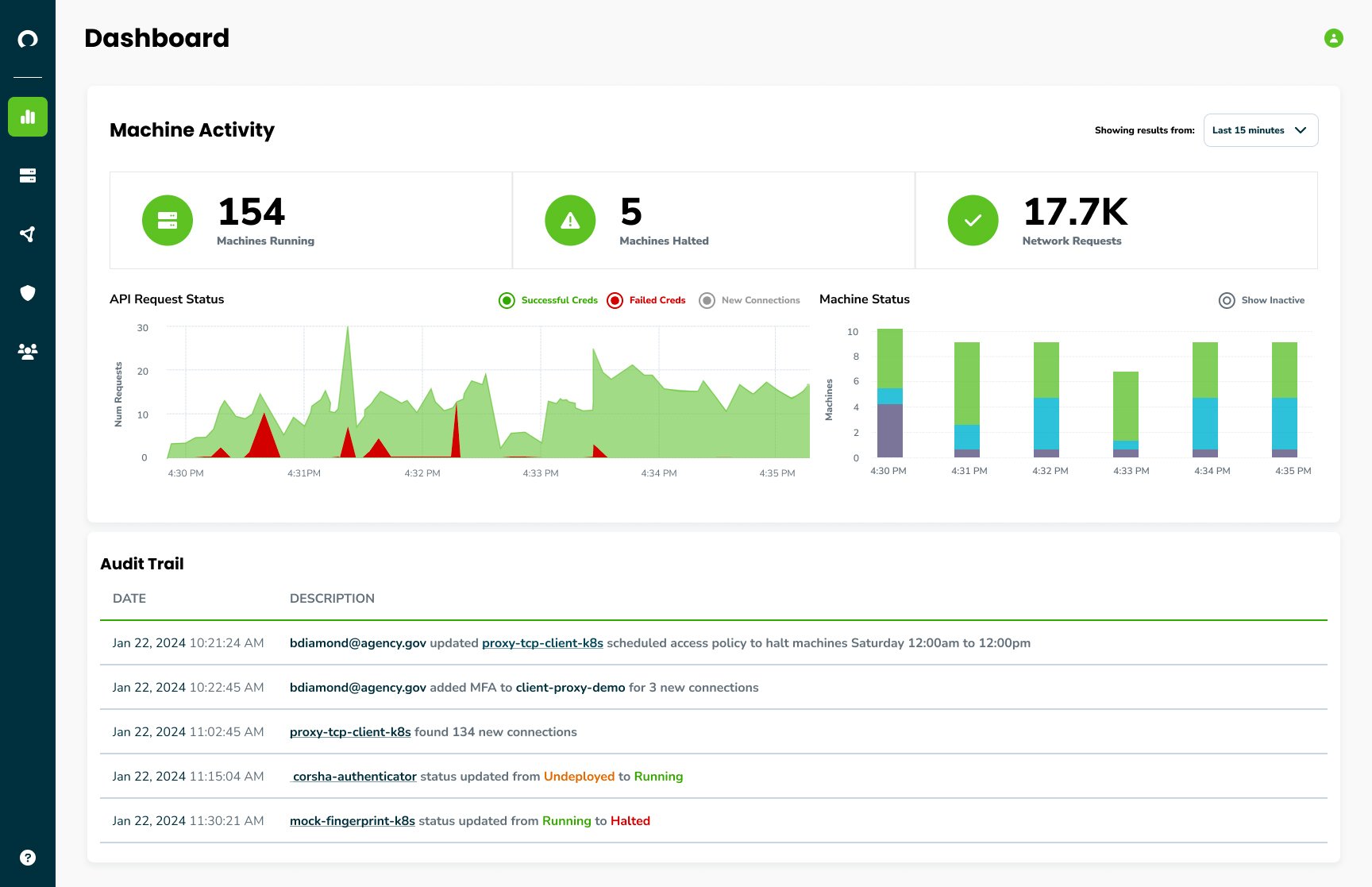
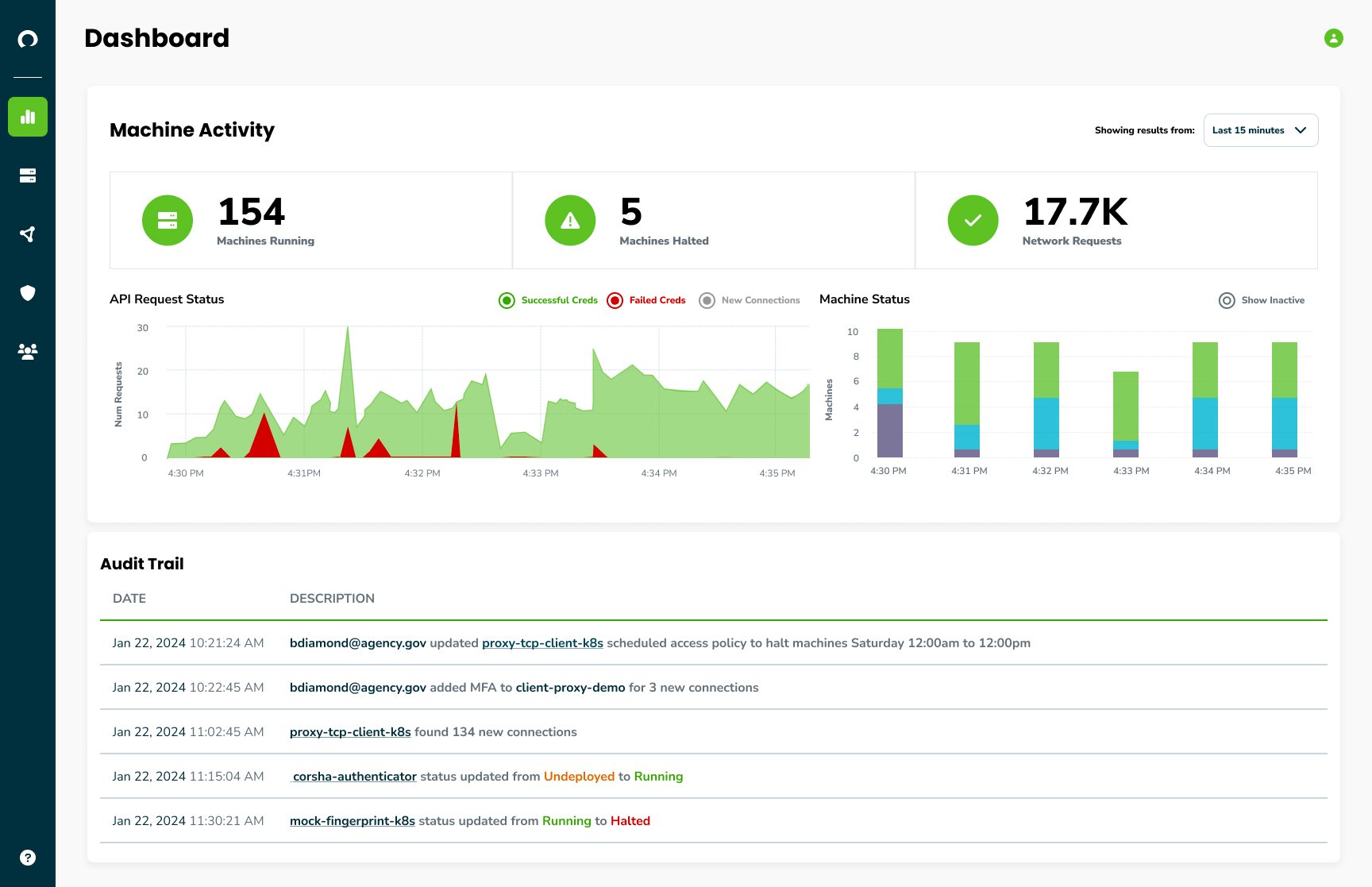
Discover and Audit Connections
Uncover, monitor, and audit every connection to your protected services, ensuring only trusted clients access your protected services and data. Streamline cryptographic identity provisioning, automate rotation, utilize short-lived PKI, and logically group machines. Elevate machines as first-class citizens across your Identity and Access Management strategy.
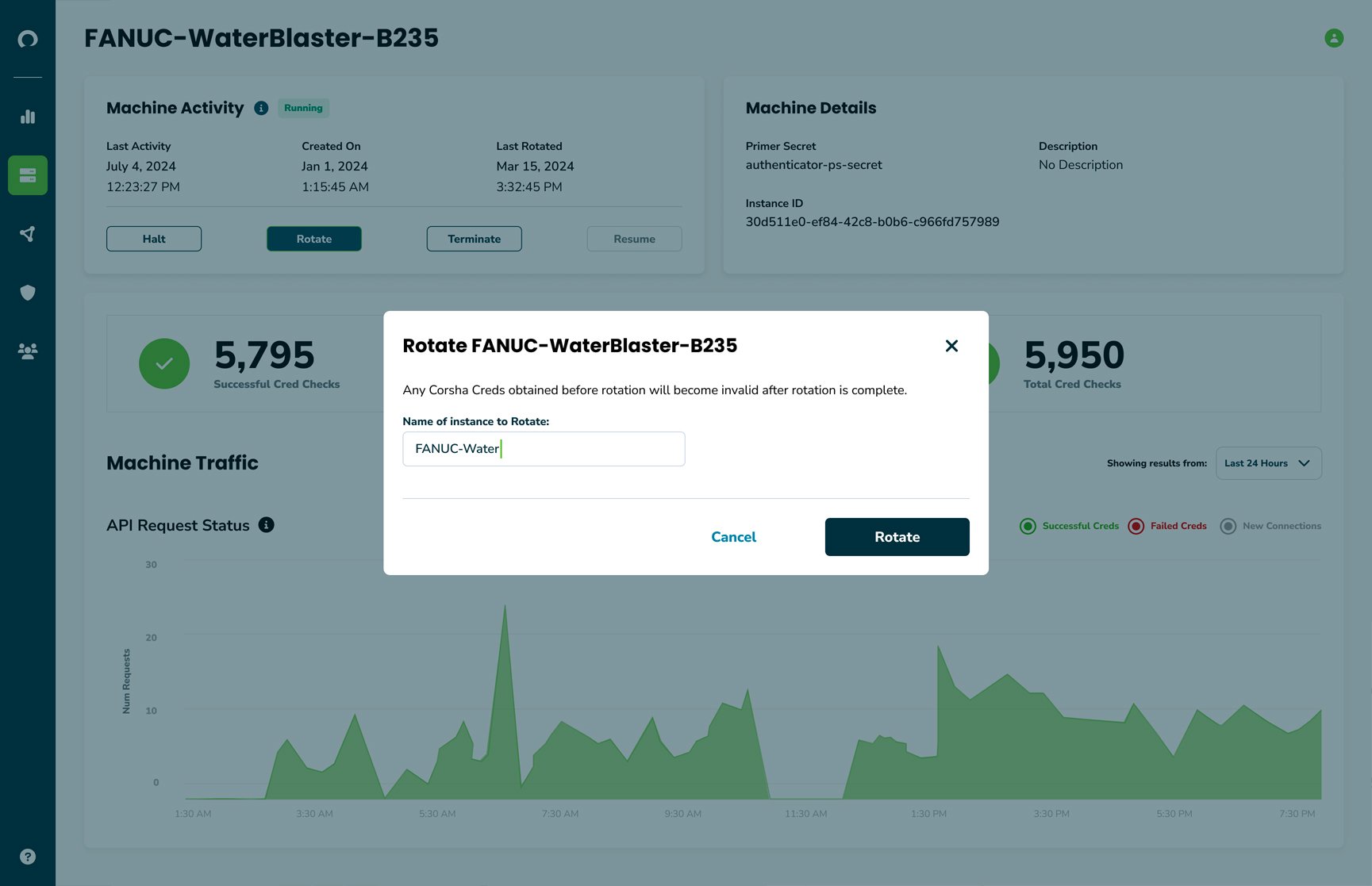
Automate Identity Rotation
Corsha’s Machine Identity Platform automatically builds dynamic identities for every one of your managed clients, letting you push past dangerous secrets sprawl. Never worry about secret rotation again and do it without putting more work on your development teams.
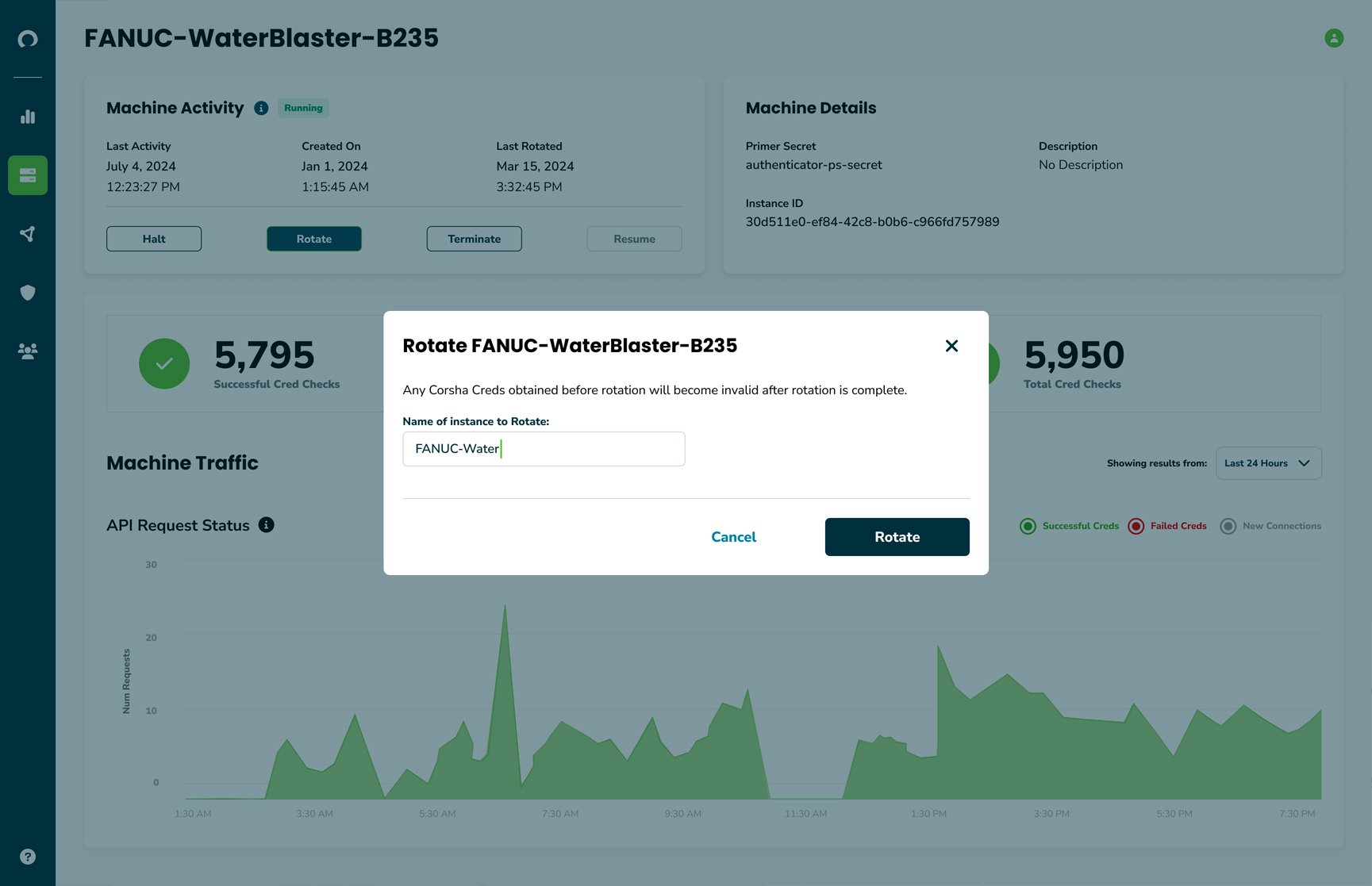
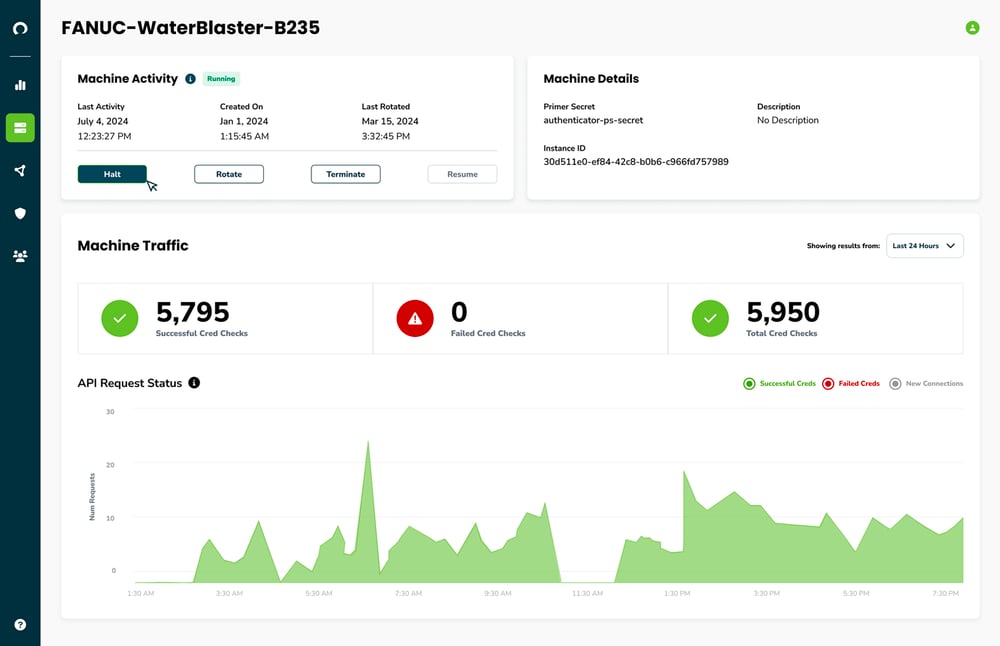
Start and Stop Access Anytime in Real-time
Corsha empowers you to respond in real-time to emerging threats and the shifting cyber landscape. With a simple click, start and stop access for a group of machines or even just a single one. This capability enables your organization to regain access control, respond in real-time to security events, and take least-privilege access to the next level.
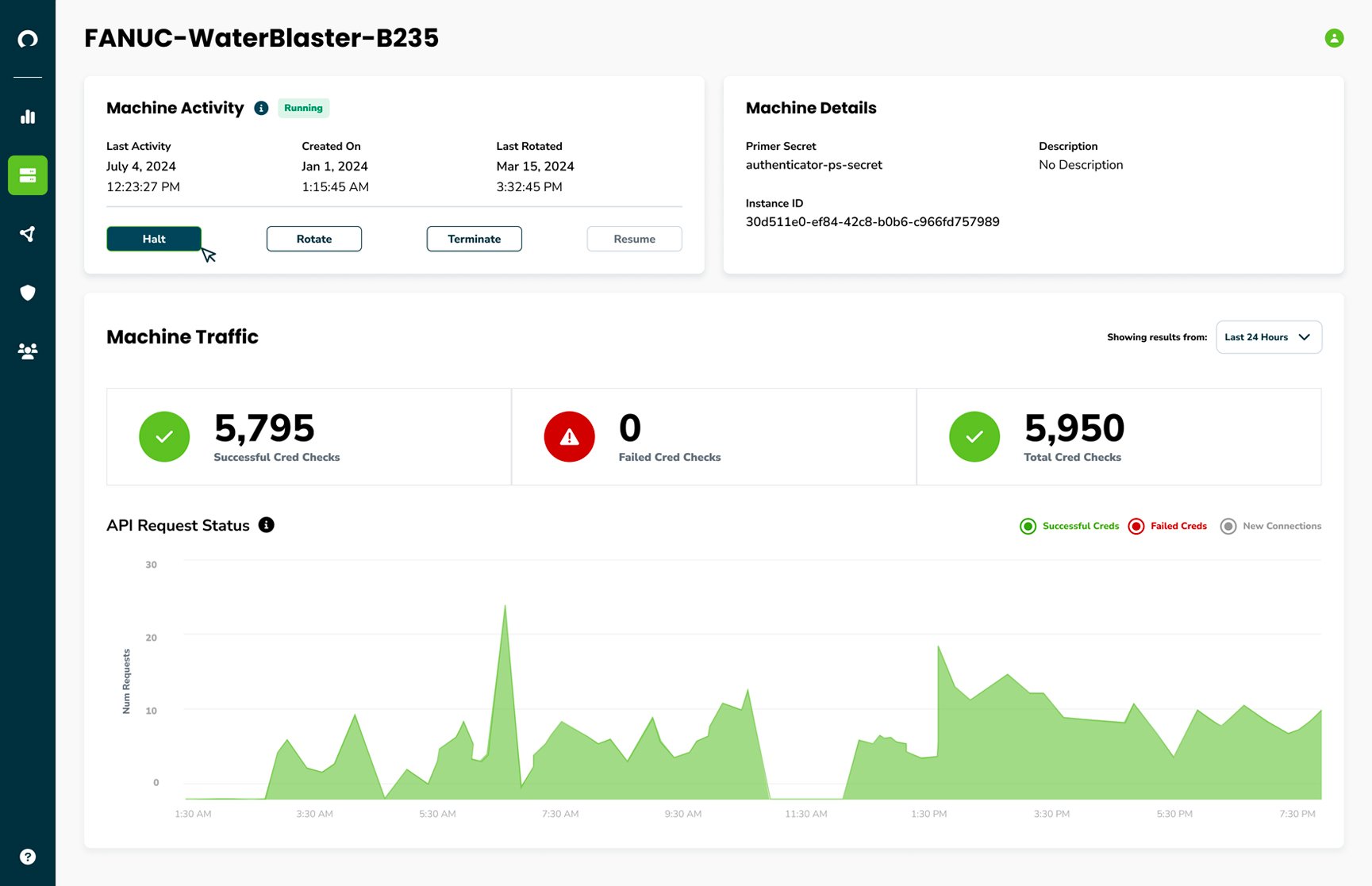
Schedule Access On your Terms
From remote vendor access to scheduled maintenance upgrades, there are various times when your protected services don't need to be open continuously and to everyone. With Corsha’s Platform, define your machine identity and access control posture to implement business operations and security policies, moving closer to adopting a zero-trust architecture today.
.png?width=1044&height=675&name=scheduled-access%20(1).png)
One-Time-Use Credentials
Corsha’s Machine Identity Platform automatically builds dynamic identities for every managed client, letting you push past dangerous secrets sprawl and never worry about certificate rotations again

No Code Change Necessary
Integrate Corsha’s solution seamlessly into your infrastructure without requiring code changes on the service or client workload side. This eliminates the need to engage vendor, OEM, or product teams to enhance identity and access management for the wide array of machines across the enterprise.
Deploy in Minutes Anywhere
Deploy Corsha's Platform in minutes on any Kubernetes cluster-supported environment. Our Infrastructure-as-Code-defined Distributed Logic Network (DLN) enables effortless horizontal and vertical scaling for enhanced flexibility.
Accredited on Government Clouds
Corsha is accredited on Government Clouds with an active continuous Authority-to-Operate (cATO) at Impact Level 2 (IL2) and IL4 moving to IL5.
Kubernetes-native and ready to deploy to any of these environments.



Securely Connect OT to IT from the Shop Floor to the Cloud and Back
Point-to-Point Access Control for your OT Equipment
- MFA for OPC-UA
- FANUC-native Integrations
- IAM across the Purdue Model
- TCP/IP for OT support
Cloud-Native Design
- Simple Helm Charts
- Inline Envoy-filters
- In the Cloud, the Edge, or On-Prem
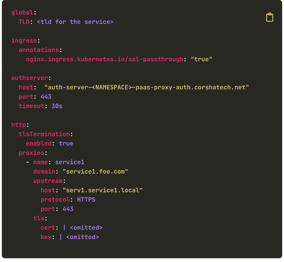
Easily integrate with API Gateways and Proxies

What Comes with Your License?
- Dedicated Customer Support
- Comprehensive Product Docs
- Commercial and Government Cloud Provider
- 24/7 Alerting and Monitoring
- Zero Trust Coverage for NPEs
- SaaS & On-Premise (Including Air-Gapped)