SOLUTIONS
Zero Trust for Non-Person Entities
Elevate NPE Identities as first-class citizens.
Zero Trust is a cybersecurity methodology that eliminates implicit trust in a network, elevates identity for all entities – human and non-human, demands continuous verification from all entities and locations, enforces least privilege, and emphasizes visibility, analytics, and automation.
.png?width=699&height=760&name=Vector%20(3).png)
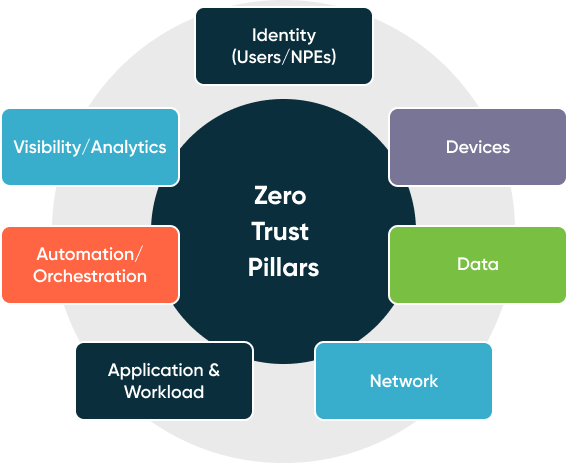
Zero Trust Guidelines
NIST, CISA, and the DoD have put together reference architectures to guide zero trust implementations.
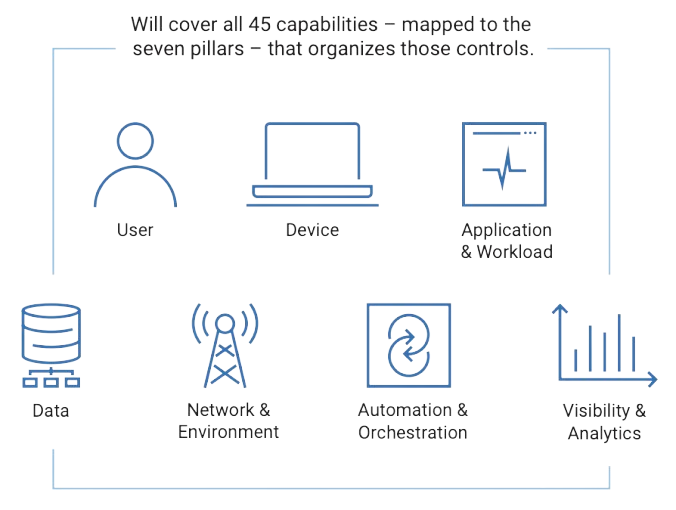
In fact, they have outlined 153 security activities across 7 pillars to achieve comprehensive zero trust across an enterprise with eager timelines to reach phases of Zero Trust compliance across the Department of Defense and the broader Defense Industrial Base.
In fact, they have outlined 153 security activities across 7 pillars to achieve comprehensive zero trust across an enterprise with eager timelines to reach phases of Zero Trust compliance across the Department of Defense and the broader Defense Industrial Base.
The Corsha Solution
Zero Trust cannot be accomplished with any single tool or vendor. It’s a strategy that takes collaboration and integration from an array of ecosystem partners. Corsha is uniquely positioned as the Identity Provider focused on Machines to satisfy many of the controls around Non-Person Entities (NPEs) across all of the 7 pillars.
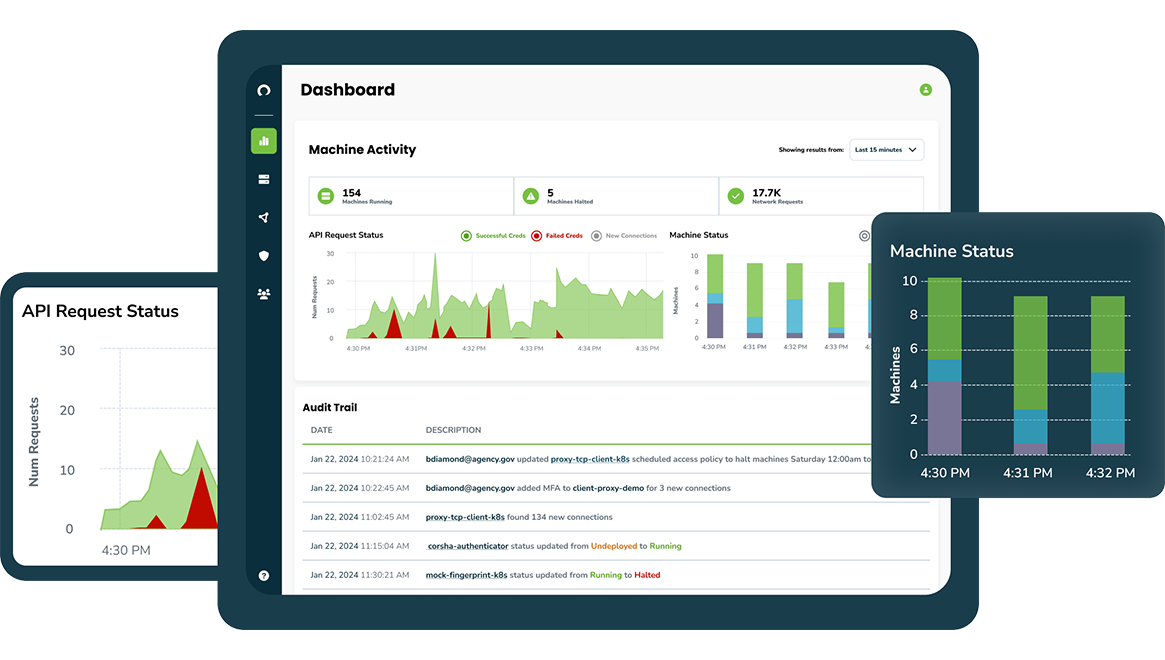



Know your machines
With strong identity and access management, you’ll now be able to understand and act on traffic
even across hybrid OT /IT environments. Develop dynamic policies for what to trust.
even across hybrid OT /IT environments. Develop dynamic policies for what to trust.
Protect data movement
With strong identity and access management, you’ll now be able to understand and act on traffic
even across hybrid OT /IT environments. Develop dynamic policies for what to trust.
even across hybrid OT /IT environments. Develop dynamic policies for what to trust.
Automate securely
Enforce one-time-use credentials even for service accounts. Enforce credential hygiene and frequent rotation with Corsha for NPEs. Move away from 3-year PKI certs.
Connect confidently
To make the most of and share data, the future is connected. Even for good security posture, data and access must move past air-gaps. Corsha provides a strong identity-first ZT NPE strategy to pin connectivity to known entities.
Leading Zero Trust Adoption
Corsha is working closely with Dell and 30 industry partners to bring to market a fully unified and accredited zero trust to speed adoption across the Federal and Commercial sectors.
.png?width=684&height=706&name=closed-catalog-mockup-lying-on-a-solid-surface-a15098%201%20(2).png)
Zero Trust for Machines Free White Paper
Zero Trust for NPEs
Read more about our Identity-first approach to Zero Trust for NPEs.

