The ongoing Digital Revolution of the past half-century is marked by the dramatic rise of information technology (IT) and the drive to connect humans with ever increasing amounts of digital information and applications to make more use of that information. During this time, operational technology (OT) systems in industrial manufacturing—programmable devices that interact with the physical environment and drive industrial output—were mostly kept in isolated, segregated enclaves.
Current ongoing modernization in the industrial manufacturing space, the so-called Fourth Industrial Revolution, or “Industry 4.0,” has created an increasing drive to connect and integrate IT and OT systems. While these developments have ushered in new efficiencies and capabilities, they have also expanded the attack surface, making industrial control systems (ICS) and operational technology (OT) increasingly vulnerable to cyber threats. This has placed immense pressure on manufacturers to not only safeguard their operations but also ensure compliance with stringent cybersecurity frameworks like NIST 800-82r3, IEC 62443, and CISA’s guidelines for critical infrastructure. As these standards evolve to address the complexities of modern manufacturing, compliance has become a major challenge, forcing manufacturers to balance innovation with the growing imperative of cybersecurity. In this blog, we introduce some of the central themes and compliance drivers behind the push towards greater cybersecurity for OT and manufacturing systems.
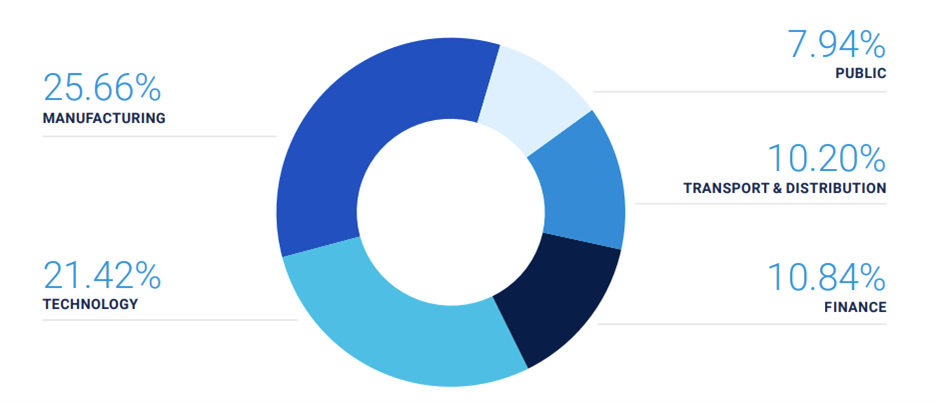
Graph: The 2024 Global Threat Intelligence Report reveals that manufacturing has now overtaken technology as the most targeted sector for adversaries.
Connectivity Drivers
The push to “connect everything to everything… everywhere” enables greater collaboration, information sharing, efficient use of resources and assets, and new technology integration to drive modern industrial operations. Ensuring secure connectivity, compliant with established and evolving cybersecurity frameworks for hybrid IT-OT networks, allows enterprises to protect vital interests and assets in the process.
The connectivity push links critical applications and data systems on the information technology (IT) side of key industrial enterprises—such as digital engineering and monitoring platforms, inventory and supply chain management systems, digital twins, and critical enterprise data repositories—to OT equipment, systems, and networks that form the process “front end” for industrial output and performance. This drives Industry 4.0 towards greater efficiency and control in industrial sectors that include manufacturing (including defense manufacturing), chemical and pharmaceutical production, energy and other utilities, food and agriculture, healthcare, transportation, and transportation.
The idea of OT-IT convergence, connectivity, and remote user and system access also allows rapid integration and utilization of new technologies beneficial to all industrial and manufacturing sectors. This includes rapidly advancing technologies such as:
-
Robotic Systems
-
Computer Numerically Controlled (CNC) Equipment
-
Additive Manufacturing System
-
Industrial IoT and Internet of Medical Things (IoMT), etc.
-
Internet of Things (IoT), Wearables, and Smart User Devices
-
Virtual and Augmented Reality Devices
-
Artificial Intelligence, Machine Learning, and Big Data Analytics Platforms
-
5th Generation (5G) Cellular and other Wireless Communications Technologies
Integrating these new connectivity-craving technologies will increasingly yield greater business productivity, cost-savings and efficiency, and process improvements. Legacy OT equipment, which was never intended to operate in a networked environment, is particularly vulnerable to cyber threats, often lacking basic cybersecurity features such as encryption or access control. The increased connectivity, while essential for Industry 4.0 advancements, creates new entry points for hostile actors who can exploit these systems to compromise both IT and OT infrastructure.
As a result, compliance with frameworks like NIST SP 800-53, which addresses security and privacy controls, and NIST SP 800-82, which focuses on ICS security (and OT systems more broadly), is no longer optional but essential for safeguarding interconnected environments.
Business Drivers
As a consequence of the connectivity and modernization push, security managers in the manufacturing space have had to take a new look at the potential these new connected technologies introduce for opening up access to IT and other business systems. The same business impact motivators that have driven IT security compliance initiatives also apply to connected OT systems, including:
-
Protecting Sensitive Company Data and Intellectual Property
-
Preventing Financial Losses
-
Reducing Operational Disruptions
-
Maintaining Reputation
-
Safeguarding Customer and Employee Trust
-
Mitigating Business Risks
-
Meeting Industry Standards
-
Complying with Government-Mandated Cybersecurity Standards
-
Avoiding Legal and Financial Penalties
While these new technologies and the push to adopt them to revolutionize manufacturing in the age of Industry 4.0 has clear benefits for industry, ensuring that they are implemented in a way that protects these core business interests is paramount. Companies must take a balanced approach, ensuring that productivity gains and cybersecurity measures remain balanced priorities in terms of these business imperatives.
Compliance Challenges
Because cybersecurity for manufacturing and other OT systems is being driven by these rapid technological advancements, and because these systems have not historically been open to the outside world in a way that significantly elevated their threat profile, a number of challenges arise to implementing cybersecurity compliance in the manufacturing space. A key early challenge is simply understanding the full inventory of equipment, often from a wide range of suppliers, and identifying their cybersecurity vulnerabilities—an essential first step in the process.
Understanding exactly which of the many complex regulatory and compliance regimes will apply to a given enterprise is also a substantial undertaking. For a U.S.-based company, there may be governing federal and state requirements that apply, as well as industry-specific standards and best practices. For companies that do business outside the U.S. or send products overseas, there will also be international requirements—including rigid data privacy frameworks in some countries—as well as an additional layer of U.S. export control compliance demands that must be considered.
Most companies will also have a limited number of cybersecurity experts that have been cultivated to deal with present IT cybersecurity concerns and the associated threat landscape. Implementing cybersecurity measures that align with compliance frameworks can be expensive, and for many manufacturers—especially small to mid-sized companies—investing in the necessary infrastructure, tools, and training feels out of reach. This means companies will have constrained resources, likely with limited OT expertise, to take on the challenge of securing these connected technologies and systems across a new range of threats, and to develop sufficient incident preparedness and response plans.
Balancing the company’s productivity with scalable security measures to ensure that the implemented solutions are cost effective will be a primary concern for business leadership and an additional challenge for security managers. To address these challenges, manufacturers can leverage phased approaches to compliance, starting with risk assessments aligned with NIST 800-53 or ISO 27001. Retrofitting legacy systems with security overlays, adopting scalable cybersecurity solutions, and integrating third-party risk management into supply chain operations can help. Creating a culture of cybersecurity awareness through training programs and prioritizing collaboration across IT, OT, and procurement teams are critical first steps in overcoming these barriers.
Conclusion
Industry 4.0 and the integration of new technologies in manufacturing promise big gains in productivity, efficiency, and cost savings. We’ve already seen the impact of robotics on sectors like automobile production. However, the benefits of IT-OT integration must be managed with a strong focus on cybersecurity to protect business interests and minimize external threats. Companies need a clear understanding of both their own infrastructure and the compliance frameworks that apply to their operations.
About Scott Hopkins
Scott serves as Corsha's Chief Operating Officer. He has over 38 years of professional experience, including 18 years of business management and operations experience with technology development companies and high-tech start-ups. At Corsha, Scott is responsible for overseeing all aspects of the company’s day-to-day business operations, and supporting strategic business planning, budget development and execution, oversight of functional operations, and business and proposal development.
About Corsha
Corsha is an Identity Provider for Machines that allows OT enterprises to securely connect, move data, and automate with confidence from anywhere to anywhere. Corsha uses Zero Trust principles to build secure identity and access to diverse OT equipment from inside or outside your industrial network and brings innovation like automated, single-use MFA credentials to machine-to-machine communications. Strong identity, access, and encryption for machines helps you track all of your connections, create a unified zero trust baseline, and securely move data across your industrial network in real-time.