At Corsha, security is a core principle in everything we build. This means carefully evaluating our software supply chain and choosing products and services that align with our rigorous standards. One key component of our DevSecOps pipeline is Iron Bank, which ensures our containerized software meets strict security requirements. Iron Bank provides a secure registry of vetted, hardened containers designed for use in critical environments, such as the Department of Defense.
What is Iron Bank?
Iron Bank is a repository of security-hardened containers managed by the U.S. Department of Defense (DoD). As part of Platform One, a DoD initiative, Iron Bank hosts containers that meet stringent security protocols, minimizing risks from vulnerabilities and misconfigurations. These containers are hardened to DoD standards, making them ideal for any environment where security, compliance, and scalability are paramount.
Why We Use Iron Bank at Corsha
Enhanced Security and Compliance
Corsha operates in a high-stakes environment where security breaches could have significant repercussions. Iron Bank gives us confidence that the containers we use meet the highest security standards, as they have undergone thorough scanning and approval. This allows us to focus on building applications, knowing our base images are secure and compliant with industry-leading protocols. The graphic below explains the continuous accreditation process for Iron Bank hardened images.
Source: https://p1.dso.mil/services/iron-bank
Efficiency in the DevSecOps Pipeline
Using pre-approved Iron Bank containers helps streamline our CI/CD processes by providing a secure foundation vetted for rigorous compliance requirements. Iron Bank’s baseline security checks, including initial vulnerability scanning, enable our developers to build on trusted images while advancing our readiness for high-assurance approvals. These include Authority to Operate under the NIST 800-53 controls, and high compliance levels, such as DoD Impact Level 5. This approach helps us maintain our efficiency without compromising on security.
Open Collaboration and Innovation
While Iron Bank is primarily a DoD initiative, it's built with an open source-ethos. At Corsha, we contribute to this ecosystem as maintainers of the InfluxDB image in Iron Bank, supporting and enhancing a trusted resource for the community. This involvement allows us to leverage both community contributions and the expertise of the DoD while actively shaping the security of key open-source components. Using Iron Bank aligns with Corsha's mission of embracing cutting-edge, open-source technologies that also meet strict operational requirements.
How We Use Iron Bank at Corsha
At Corsha, Iron Bank images serve as a foundation for our container-based workflows. While Iron Bank provides a strong baseline with compliance-tested images, we integrate additional security layers by using Trivy scanning throughout our pipeline. Integrating Trivy scans in our pipeline enables us to continuously monitor for newly discovered vulnerabilities that might emerge after an image has been created. This approach ensures that any vulnerabilities introduced post-build are identified and mitigated before deployment, enhancing the security and resilience of our services.
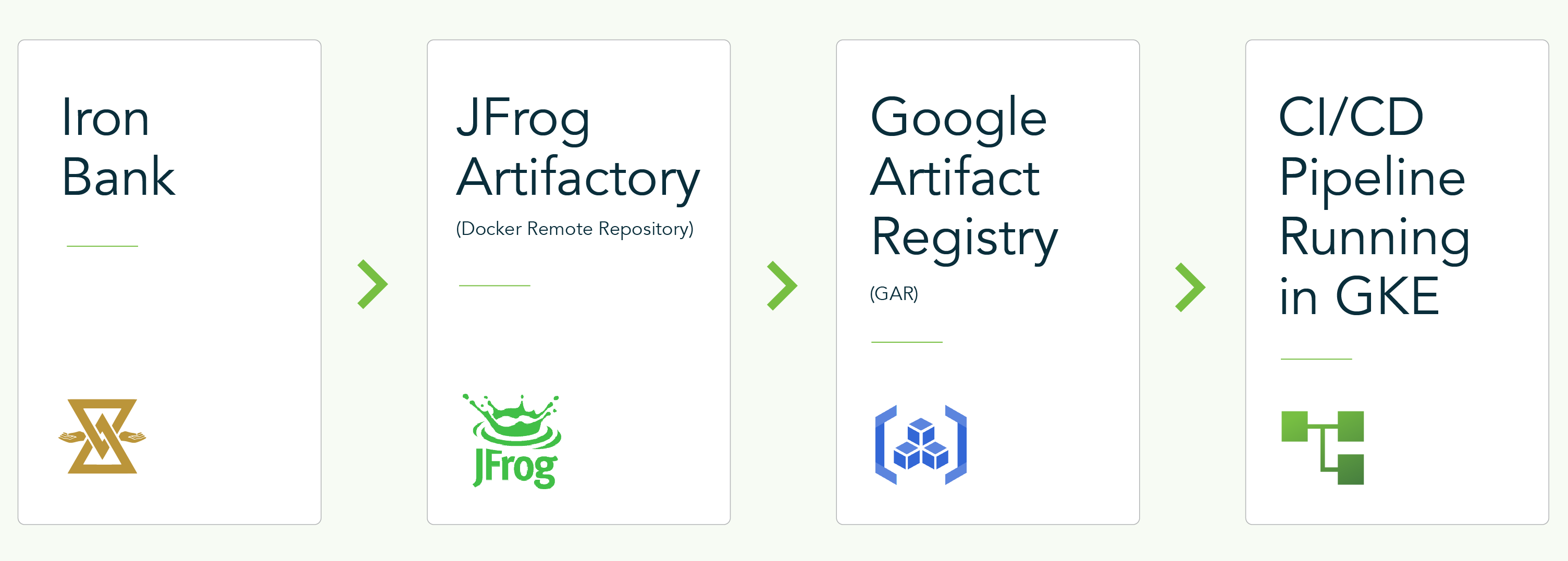
To optimize availability and performance, we maintain a Docker remote repository in JFrog Artifactory, which we mirror to Google Artifact Registry (GAR). This strategy offers several benefits, including improved image availability, enhanced performance, and cost savings. Since we primarily use Google Kubernetes Engine, having copies of our critical Iron Bank images in GAR significantly reduces our cloud expenses, as Google does not charge for data transfers within the same location.
Alternatives to Iron Bank
Iron Bank is a popular choice for hardened containers, but it is not the only option. Chainguard is an appealing alternative, offering low-to-zero CVE container images.
Like Iron Bank, Chainguard images are built and scanned daily. While Iron Bank is freely accessible for public use and contributions, Chainguard, a privately owned company, charges for most of its images. However, Chainguard currently publishes a selection of its free, developer-tier images directly to Iron Bank, making Iron Bank a convenient platform to trial Chainguard images alongside its own extensive offering of hardened containers.
Conclusion
In today's high-stakes cybersecurity landscape, we have found Iron Bank to be a valuable tool in securing our software supply chain. It helps us maintain compliance, mitigate risk, and ensure the trustworthiness of our applications, allowing our developers to focus on innovating at the application level.
About Christian
Christian Petersen is a DevOps specialist focused on Infrastructure as Code (IaC), security, and automation. His expertise includes managing Kubernetes clusters, optimizing CI/CD pipelines, and integrating robust security practices across the development lifecycle.
About Corsha
Corsha is an Identity Provider for Machines that allows an enterprise to securely connect, move data, and automate with confidence from anywhere to anywhere.
Corsha’s mission is to secure data in motion and bring zero trust to machines, systems, and services. Today Ops and security teams often are forced to compromise by using static, long-lived API keys, tokens, and certificates as weak proxies for non-human identity and access. Corsha helps teams move past static secrets and generates dynamic identities for trusted machines, bringing innovation like automated, single-use MFA credentials, scheduled access, and deep discovery to machine-to-machine communications. The Identity Provider also offers visibility and control over automated API traffic and enables real-time revocation and rotation of identity without disrupting other workloads.




