
Blog

By Corsha
on December 08, 2023
on December 08, 2023

By Corsha
on October 31, 2023
on October 31, 2023

By Corsha
on October 04, 2023
on October 04, 2023

By Corsha
on September 27, 2023
on September 27, 2023

By Corsha
on September 19, 2023
on September 19, 2023

By Corsha
on September 05, 2023
on September 05, 2023

By Corsha
on July 25, 2023
on July 25, 2023

By Corsha
on July 12, 2023
on July 12, 2023



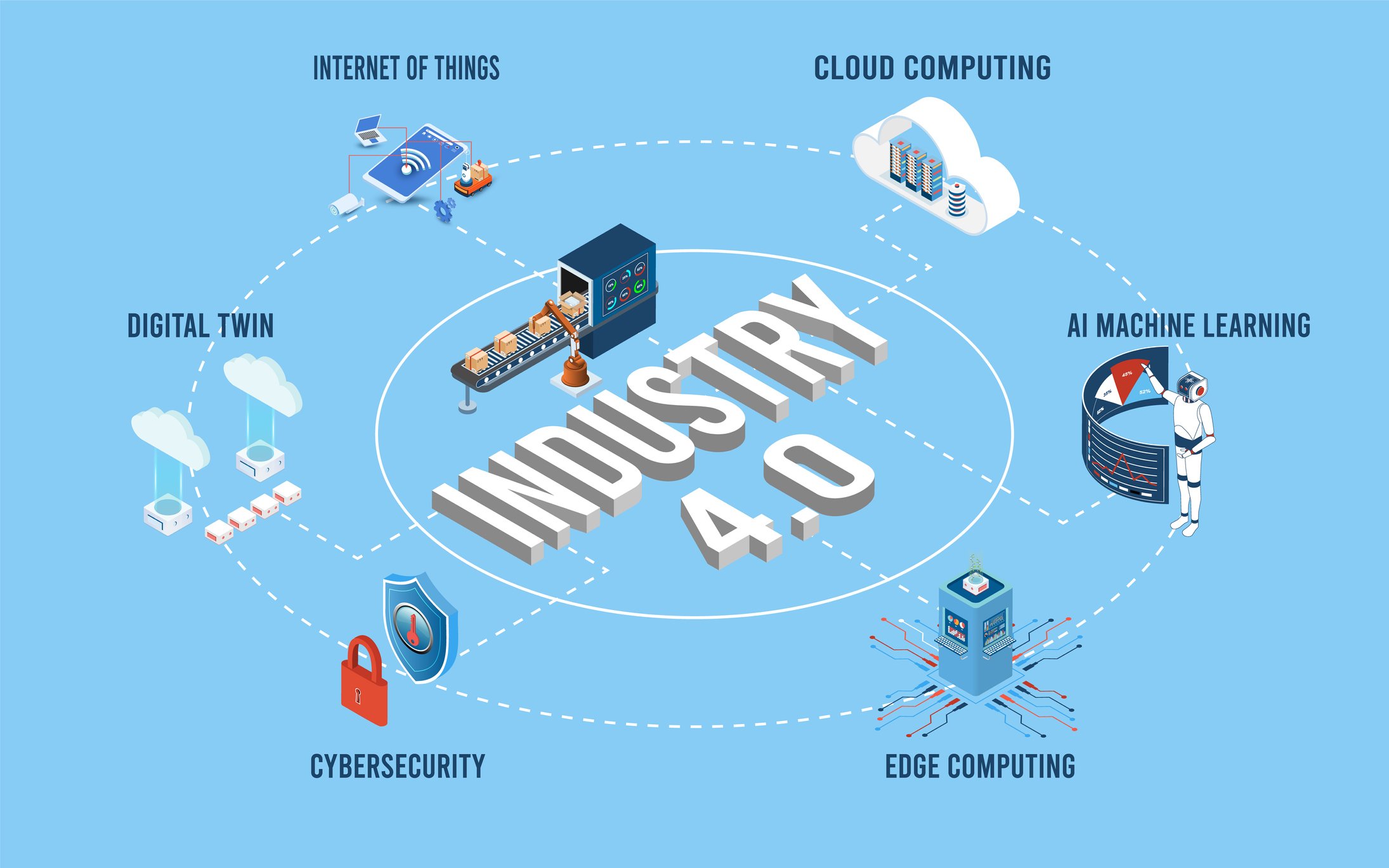
-1.png)
-3.png)
.png)


.png)
